Malware Reverse Engineering
 As the title of this blog states, this short blog is about malware reverse engineering. This seems to be a very popular topic among security experts. The idea of reverse engineering of malware is to find out what weakness did the malware expose on your side (network, operating system, etc).
As the title of this blog states, this short blog is about malware reverse engineering. This seems to be a very popular topic among security experts. The idea of reverse engineering of malware is to find out what weakness did the malware expose on your side (network, operating system, etc).
After researching for approximately 3 days, this is one tough area to learn. Assembly language and system calls are the two objectives that you are looking into when dissembling malware. The system I used is Late 2013 iMac with a Windows 7 virtual machine installed on it. The virtual machine is isolated and is not connected to the network. I did use a dissembler which was used for static analysis. Debugger is great because it provides you with a great sense of on the fly action that the malware migh execute. Debuggers that I consider valuable are: IDA Pro, Immunity Debugger and Oly Debugger. The one I spent most time on was IDA Pro. Keep in mind that these tools are not cheap. IDA Pro for example Starter edition is USD$589 and Pro is US$1129. I do believe this particular area will see significant growth as Malware becomes more sophisticated and the attacks turn toward mobile users.
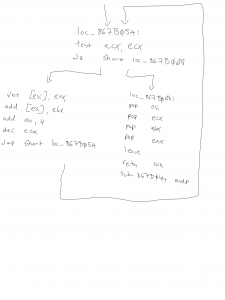
What was I able to do in 3 days? Take a look at the diagram above. I did manage to dissemble one particular type of Malware, however my skills are fairly basic in this area, and I’m unsure if I got all the systems calls. This was a Windows based Malware, see if you can guess what Malware it is?

Leave a Reply
Want to join the discussion?Feel free to contribute!